My First Crackme!
Published on 2025-01-08
Category: Misc
In this post, we explore a Windows x86-64 crackme from crackmes.one called noxy's lv10 easy crackmes, authored by noxys. We’ll use a Windows environment and FLARE VM for analysis. Let's see how to tackle missing DLL errors, examine suspicious strings, and pinpoint the hidden password.
Setting Up the Lab
I used a Windows machine equipped with FLARE VM as my main lab to work on this crackme.
Initially, I scanned the crackme’s ZIP file with VirusTotal, and 3 out of 73 security vendors flagged it as a trojan.
After extracting the ZIP with 7-Zip, I found an executable named lvl0.exe.
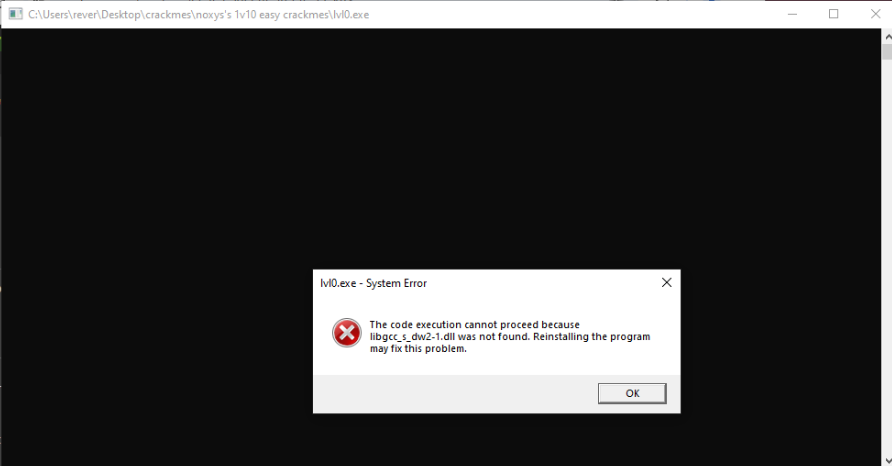
When I tried running lvl0.exe, I encountered the following errors:
- The code execution cannot proceed because
libgcc_s_dw2-1.dllwas not found. - The code execution cannot proceed because
libstdc++-6.dllwas not found.
To fix this, I decided to compile the source code with MinGW since it has the C++ libraries needed. Once compiled, I ran the new executable and saw a prompt saying:
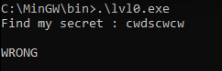
Find my secret:
Entering a random string resulted in the output WRONG.
Initial Analysis with Strings
We'll first use the strings utility on lvl0.exe. This can reveal
human-readable text that might hint at a correct password or highlight interesting functionality.
The binary included many references related to GCC 6.3.0, MinGW, and standard C++ library symbols—typical for a C++ program compiled on Windows using MinGW. Then I spotted more unique strings, including:
C++ is bestDota 2 >>>>> LoLPython is trashHate from africam not crazyfentanylimgayFind my secret :Correct DaDdYYYYWRONG
The “Find my secret:” prompt clearly matches what we see at runtime, so I suspected one of these other odd strings might be the correct password.
Finding the Correct Password
I tried inputting each suspicious phrase from the list. After several “WRONG” messages,
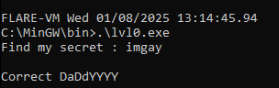
I discovered that imgay is the winning password.
The program then printed Correct DaDdYYYY to confirm success.
Sometimes, developers embed an actual password within success strings. In this case,
the presence of “imgay” was enough to solve it. The weird random strings might be red herrings
or included just to throw off anyone sifting through strings. It seems we got lucky!
Conclusion
Overall, noxy's lv10 easy crackmes provided a quick and straightforward puzzle:
dealing with missing DLLs, analyzing suspicious strings, and discovering the secret prompt.
Always remember to check a crackme with tools like strings for potential clues, especially
for simpler challenges. If you encounter missing Win libraries, recompiling the code with MinGW or
installing the required DLLs can help you run the executable without errors (most of the time).
happy cracking!
